The Visibility Problem with MicroVMs
MicroVMs, lightweight virtual machines that combine the isolation of traditional VMs with the speed and efficiency of containers, represent the next evolution in cloud-native security. By running each workload in its own lightweight virtual machine with a dedicated kernel, technologies like Edera provide hardware-level isolation that dramatically reduces the attack surface compared to traditional containers. This hardware-level separation is why AWS Lambda, Google Cloud Run, and other serverless platforms rely on microVM technology to safely run untrusted code at scale.
But this enhanced security creates a challenge for security teams: traditional monitoring tools can't see what's happening inside microVMs.
Falco leverages custom rules on Linux kernel events using kernel probes (kprobes) or eBPF, depending on configuration to provide runtime security across hosts, containers, and Kubernetes environments. When workloads run in isolated microVMs rather than sharing the host kernel, security teams lose the visibility they depend on for threat detection and compliance.
This isn't just a technical inconvenience – it's a deal-breaker for many organizations. Security and platform teams shouldn't have to choose between secure container isolation and operational visibility. They need both.
"Falco has become the open standard for Kubernetes runtime detection, and for good reason. As we researched solutions for improving workload isolation and security, maintaining our existing Falco-based workflows without losing signal fidelity was a critical requirement,” said Jon Ceanfaglione, Chief Architect, DevSecOps, IBM Federal Consulting. With Edera, Falco's proven detection capabilities now extend seamlessly into our microVM workloads, combining the CNCF community's trusted tooling with next-generation isolation. It's the best of both worlds for our cloud-native infrastructure."
"Falco was built for the community, and it continues to be strengthened by the community," said Leonardo Grasso, Falco Maintainer and Technical Lead for Open Source Engineering at Sysdig. "Edera's integration with Falco builds on the real-time threat detection capabilities that have made it the industry standard for cloud-native environments, and extends those protections to microVMs."
How the Integration Works
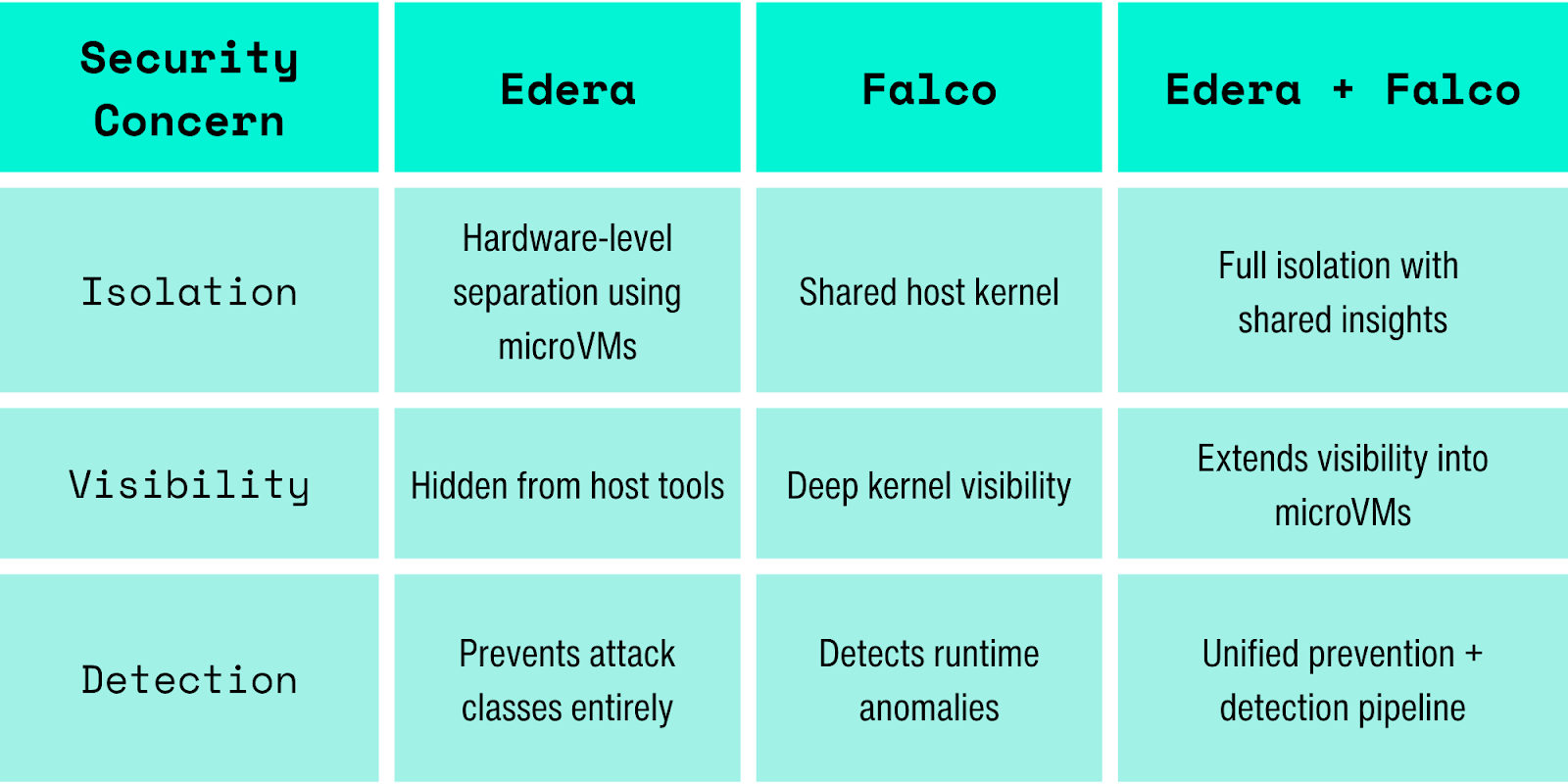
Our integration with Falco ensures that security teams maintain complete visibility into their workloads, regardless of where they run. MicroVMs provide true hardware-level isolation between workloads, and now Falco can monitor them just as effectively as traditional containers.
We've built a native Falco plugin that seamlessly exchanges syscall events from Edera zones (our microVMs) to your existing Falco deployment. The integration leverages Falco's stable plugin API and wraps Falco's libscap library to ensure complete syscall coverage. This means:
- Reuse existing rules: Rescope your existing Falco rules to the `edera-zone` source and you’re off to the races with your Edera workloads.
- Consistent event format: Zone events appear in the same format as host events
- Intelligent filtering: We automatically mirror Falco’s existing syscall filtering into Edera workloads to optimize capture performance
- Easy deployment: Install via standard Falco plugin management tooling
The technical approach is elegant: we deploy Falco's battle-tested eBPF instrumentation inside each zone, stream events to the host through our secure inter-domain communication channel, and deliver them to your Falco agent through our plugin. Your security team gets a unified view across all workloads—whether they're running as traditional containers or in hardened microVMs.

Why This Matters
For security teams, this integration means you can adopt stronger workload isolation without sacrificing the runtime detection capabilities you rely on. Continue using your proven Falco rules and workflows while benefiting from hardware-backed isolation. Forward alerts to your existing SIEM, maintain compliance, and respond to threats with the same tools and processes you've already established.
But there's an added benefit: you can actually reduce your security overhead. Because Edera's microVM isolation eliminates entire classes of threats at the kernel level – container escapes, privilege escalation attacks, and cross-workload contamination – you can safely deprioritize the Falco rules designed to detect those threats. Fewer rules means fewer false positives to triage, clearer alert prioritization, and reduced data volume flowing to your SIEM. For organizations ingesting thousands of security events daily, this translates to meaningful cost savings on SIEM licensing while simultaneously improving your security team's signal-to-noise ratio.
For platform engineering teams, this removes a major barrier to adopting microVM technology. You no longer need to rebuild your entire security observability stack to gain superior isolation. Deploy Edera's microVM runtime, enable the Falco plugin, and your existing security monitoring continues working seamlessly—with better economics and operational efficiency.
For the cloud-native ecosystem, this integration demonstrates that enhanced security and operational visibility can coexist. As Falco provides runtime security that's ready out-of-the-box with customizable rules, teams can now extend that proven detection capability to workloads that demand the strongest isolation available in Kubernetes.
Available Today at KubeCon Atlanta
The integration is available now for Edera customers. Documentation, installation guides, and the Falco plugin are available in our docs.
Stop by our booth (#2041) to see Edera in action, or reach out to schedule a technical deep-dive with our engineering team on site.
Because when it comes to cloud-native security, superior isolation and comprehensive visibility go together – like peaches and cream.

