What is Confidential Computing? From Encrypted Execution to Zero-Trust Workloads
This blog is a part of our “WTF is...?” series that cuts through the noise to explain complex and trending topics in plain English. We break down the jargon, skip the fluff, and give you the essential knowledge you need to understand what’s what. Whether it's emerging technology, industry buzzwords, or confusing concepts, we strive to make it accessible.
What the f*ck is confidential computing, and why should you care? If you have sensitive data that you want kept private from other users of a machine, you might be interested in confidential computing. By the end of this post, you’ll have a clear, no-BS understanding of what confidential computing is, why it matters, and how it shapes the way we build secure, efficient systems today.
What Is Confidential Computing?
In plain English: Confidential computing is a hardware-based approach that enables your data to be encrypted while in use.
Think of it like storing your valuables within a bank. Confidential Computing is like the safety deposit box in a sealed room where you can view your valuables, but instead of having to go into the bank, you can access your valuables from your laptop. You can work away in privacy, and at a level that even the bank that owns the building can’t see what you’re working on.
Why Confidential Computing Matters for Security
Confidential computing isn’t just technical trivia – it exists to solve a real problem: running data in an untrusted environment.
For security leaders, this means:
- Your data is encrypted in use: not just while in transit and at rest.
- You can securely run workloads in an untrusted environment
- You can move trust from your cloud provider to a hardware trusted execution environment (TEE).
How Confidential Computing Works (Step-by-Step)
At a high level, here’s how confidential computing works:
- You do remote attestation to verify the state of the TEE
- Send data to the verified TEE
- Your application runs with all code and data encrypted in use!
That’s it – no jargon, just the basics.
How Edera Enhances Confidential Computing
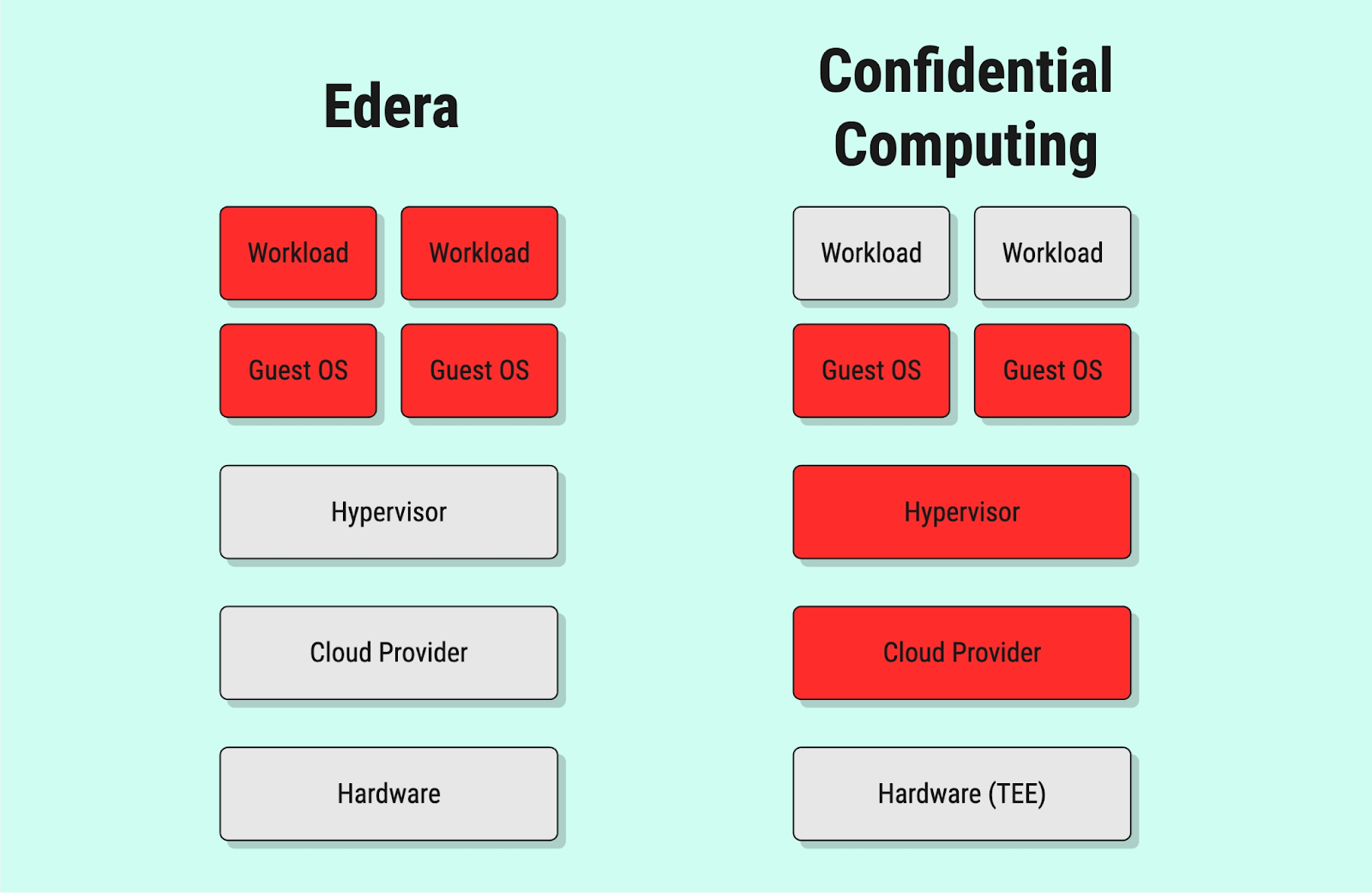
Here’s where it gets interesting: You can combine Edera and confidential computing to get both encryption in use and secure isolation to protect your infrastructure from untrusted workloads. Even if you don’t have access to a hardware TEE, you can use Edera Confidential Core to get many of the benefits of confidential computing without the reliance on hardware.
Instead of forcing a tradeoff between insecure workloads and expensive hardware, our approach with Edera Confidential core delivers security and isolation – without compromise.
Common Confidential Computing Misconceptions
A few things people usually get wrong about confidential computing:
Myth: Confidential computing protects your data from the rest of the stack.
Reality: Confidential computing means you don’t have to trust your cloud provider, but you’re still vulnerable to problems with the TEE or in your workload itself.
Myth: Confidential computing is only for highly sensitive or regulated applications
Reality: Confidential computing can provide protection for data in use for anyone with sensitive data or intellectual property.
Myth: Confidential computing prevents all software attacks.
Reality: While confidential computing protects against a compromised operating system, cloud provider, or hypervisor, it does not eliminate vulnerabilities in your application itself.
If you want more myth busting, I dive deeper into common misconceptions in my blog post here.
Key Takeaways on Confidential Computing
At the end of the day, confidential computing is really just a piece of hardware that lets you encrypt an application and its data. This ensures that other applications on the system and even the operating system itself can’t interfere with your sensitive data.
FAQs
What is confidential computing in simple terms?
Confidential computing uses a trusted execution environment to encrypt an application and its data while in use.
Why is confidential computing important for containers?
Confidential computing means you can use cloud infrastructure without needing to trust your cloud provider with sensitive data.
What’s the difference between confidential computing and homomorphic encryption?
While both confidential computing and homomorphic encryption allow for data to be encrypted in use, confidential computing uses a hardware TEE to achieve this, while homomorphic encryption uses mathematical principles to enable computation directly on encrypted data.
Does Edera use confidential computing?
Edera is compatible with confidential computing, and the two can be combined to achieve both workloads isolated from their infrastructure, and protection of infrastructure from compromised workloads.
Want to learn more? Check out our full WTF is that? Series and our Confidential Computing series.

-3.png)